Should Privileged Access Management Be Your Next Step in Cybersecurity?
Privileged accounts, known as superuser accounts, are primarily used for administration by specialized IT employees and provide virtually unrestrained power to execute commands and make system changes. Since 74% of breaches involve privileged credentials, it might be time for your company to take a closer look at how secure your systems are.
Are your systems safe?
Privilege Related Risks and Threats
The mismanagement of privileged accounts may expose a company’s entire system to attackers. Here are a few examples of some common risks and issues companies may encounter.
- Sharing accounts and passwords: IT teams often share credentials with one another, thereby making it difficult to tie actions back to a single individual. This creates security, auditability, and compliance issues.
- Over provisioning privileges: Granting access to more privileges than necessary. These excessive privileges increase the ability for hackers to leverage the entire set of privileges of the account to access data and attack systems.
- Authorization creep or privilege creep: An issue that is incredibly common in large organizations, where privileges assigned to a user are never revoked, even when the user does not need them anymore.
- Lack of awareness of privileged users: Tying in to authorization creep, these are long forgotten privileged accounts that could provide dangerous backdoors for attackers. For example, former employees who have left the company but still have access to accounts.
- Pivoting: The pivot is when the attacker first gains access to the employee computer and “pivots” from that system to another system on the same network to gain further access to the target.
So, what is Privileged Access Management (PAM)?
Privileged access management (PAM) involves the cybersecurity strategies and technologies used to control the privileged access for users, accounts, processes, and systems across an IT environment.
By applying the appropriate level of controls, PAM helps organizations condense their attack surface, and mitigate the damage arising from external attacks, insider malfeasance or negligence.
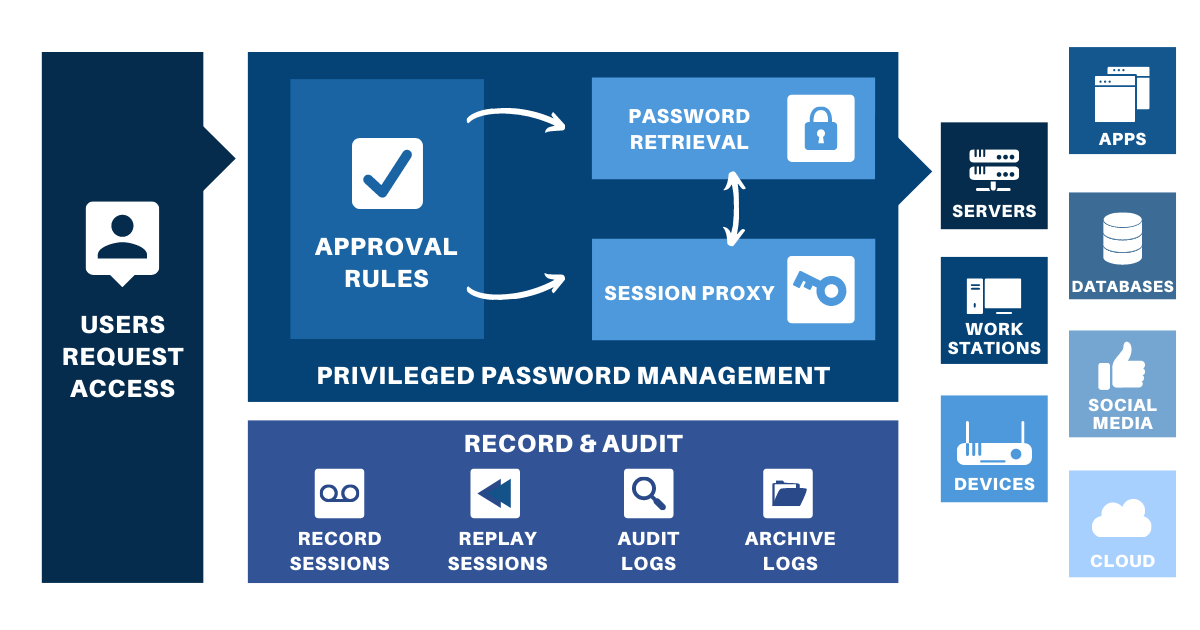
How a basic PAM system works (source: BeyondTrust)
PAM uses a least privilege approach, where no matter the user, their access rights and permissions to accounts, applications, systems, etc. are restricted to the absolute minimum needed to perform authorized activities.
Implementing privilege management not only minimizes the potential for a security breach occurring, it also helps limit the scope of a breach should one occur.
What sets PAM apart from other types of security technologies is that PAM can dismantle multiple points of the cyberattack chain. Thereby, providing protection against both external attacks as well as attacks that make it within networks and systems.
How does PAM help?
- Provides a condensed attack surface that protects against both internal and external threats, which reduces the pathways and openings for exploitation
- Monitors and tracks privileged activities, and detects suspicious activity during privileged sessions
- Using a least privilege approach reduces malware infection and can prevent malware from gaining a foothold
- Enhanced operational performance
- Easier to achieve compliance by helping to create a less complex, and more audit-friendly, environment
Having everything on one system may sound daunting, however PAM is considered by many analysts as one of the most important security projects for reducing cyber risk and achieving high security ROI.
Get in touch with us at info@kbsl.com to learn how you can upgrade your system today!
